Introduction to Cryptography
Cryptography is the practice of creating secure communications by converting information into a format that is unreadable by unauthorized parties. It is an essential field in computer science and information security.
The main goal of cryptography is to ensure the confidentiality, integrity, and authenticity of data. By encrypting information, it becomes illegible to anyone who does not possess the necessary keys or passwords to decrypt it. This makes it virtually impossible for hackers or eavesdroppers to access or understand the original message.
There are two types of cryptography: symmetric-key cryptography and public-key cryptography.
Symmetric-key cryptography involves using a single shared key to encrypt and decrypt messages. The sender and receiver must possess the same key, which needs to be kept secret. This method is faster and more efficient but requires a secure method of distributing the key.
Public-key cryptography, on the other hand, uses a pair of keys: a public key and a private key. The public key is freely distributed, while the private key is kept secret. Messages encrypted with the public key can only be decrypted with the corresponding private key. This method is slower but eliminates the need for a secure key distribution process.
Cryptography also includes various algorithms and protocols to secure data and communication. These include cryptographic hash functions, which generate fixed-size unique outputs for given inputs, and digital signatures, which provide proof of authenticity and integrity.
In addition to securing information, cryptography is also used for other purposes such as authentication, key exchange, and secure electronic transactions. It is widely used in technologies such as online banking, secure messaging, and e-commerce platforms.
Overall, cryptography plays a crucial role in ensuring the confidentiality and security of sensitive information in today’s digital world, allowing for secure communication and transactions.
Types of Cryptographic Techniques
Cryptography is the practice of securing communication and data by converting plain text or data into an unreadable format, known as cipher text, using various cryptographic techniques. There are several types of cryptographic techniques used in different scenarios to achieve confidentiality, integrity, authentication, and non-repudiation. Here are some common types of cryptographic techniques:
1. Symmetric Key Encryption: Symmetric key encryption uses a single key to both encrypt and decrypt data. It is fast and efficient, suitable for encrypting large amounts of data. Examples of symmetric key algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES).
2. Asymmetric Key Encryption: Asymmetric key encryption, also known as public-key encryption, uses a pair of unique keys – a public key for encryption and a private key for decryption. It allows secure communication between two parties without the need to share a secret key. Popular asymmetric key algorithms include RSA, Diffie-Hellman, and Elliptic Curve Cryptography (ECC).
3. Hash Functions: Hash functions are algorithms used to create a unique fixed-size digest, called a hash value or message digest, from input data of any size. They are commonly used for data integrity verification and digital signatures. Examples of hash functions include SHA-256 (Secure Hash Algorithm 256-bit) and MD5 (Message Digest 5).
4. Digital Signatures: Digital signatures provide a means of verifying the authenticity and integrity of digital messages or documents. It uses asymmetric key encryption, where the sender signs the message with their private key, and the recipient can verify it using the corresponding public key. Digital signatures utilize the principles of hash functions.
5. Key Exchange: Key exchange protocols allow parties to securely establish a shared secret key over an insecure communication channel. These protocols ensure that no one other than the communicating parties can determine the shared key. Examples of key exchange protocols include Diffie-Hellman and Kerberos.
6. Steganography: Steganography hides secret messages or data within innocent-looking cover objects like images, audio, or video files. It aims to conceal the existence of the message, rather than its content. Steganographic techniques include hiding data within the least significant bits of an image, or altering the color values slightly to encode information.
7. Quantum Cryptography: Quantum cryptography leverages principles from quantum mechanics to provide secure communication channels. It takes advantage of the properties of quantum physics, such as quantum key distribution using photons, to enable secure communication and encryption resistant to quantum computers’ computing power.
These cryptographic techniques are used in combination or individually to ensure secure communication and protect sensitive information across various digital platforms and applications.
Applications of Cryptography
Cryptography has a wide range of applications across various fields. Some key applications of cryptography include:
1. Secure Communication: One of the primary applications of cryptography is to ensure secure communication between two or more parties. Cryptographic algorithms are used to encrypt data and transmit it securely over an insecure channel. This is widely used in protocols like Secure Sockets Layer (SSL), Transport Layer Security (TLS), and Virtual Private Networks (VPNs) to secure internet communications.
2. Data Protection: Cryptography is used to protect data stored on various devices, such as computers, mobile phones, or cloud storage services. Encryption algorithms are applied to sensitive data to prevent unauthorized access, ensuring its confidentiality. This is commonly used for protecting personal information, financial data, and other sensitive data.
3. Authentication: Cryptography is utilized to verify the authenticity of messages or identities. Digital signatures are used to ensure the integrity and non-repudiation of electronic documents or transactions. Public key infrastructures (PKIs) are often employed for authenticating parties in secure communication systems.
4. Secure Transactions: Cryptography plays a crucial role in securing online transactions, such as e-commerce and online banking. It ensures the confidentiality and integrity of financial transactions by encrypting sensitive data like credit card numbers, passwords, and transaction details. This prevents unauthorized access or tampering of the transaction data.
5. Password Protection: Cryptographic techniques are employed to store and protect user passwords. Hash functions are commonly used to transform passwords into irreversible, fixed-length values called hashes. This ensures that even if a password database is compromised, the original passwords remain unknown.
6. Digital Rights Management (DRM): Cryptography is utilized in DRM systems to protect digital content from unauthorized copying or distribution. Encryption algorithms are used to scramble the content, and decryption keys are provided to authorized users, enabling them to access the content while preventing unauthorized usage.
7. Blockchain Technology: Cryptography is an integral part of blockchain technology, which underpins cryptocurrencies like Bitcoin. It is used to secure transactions, create digital signatures, and ensure the immutability of data stored on the blockchain. Cryptographic algorithms help maintain the integrity and security of the distributed ledger.
8. Privacy Preservation: Cryptography is employed to protect individual privacy in various scenarios. Techniques like secure multiparty computation (SMC), homomorphic encryption, and zero-knowledge proofs enable computations on encrypted data without revealing the underlying information. This ensures privacy while allowing data analysis and collaborative computation.
Overall, cryptography is essential for maintaining the security and privacy of digital communications, transactions, and sensitive data, enabling secure and trustworthy interactions in the digital realm.
Breaking Cryptographic Systems
Breaking cryptographic systems is the act of deciphering or bypassing the security measures put in place to protect sensitive information. Cryptography is the practice of using mathematical algorithms to encrypt data in order to ensure its confidentiality, integrity, and authenticity.
There are various techniques and methods used to break cryptographic systems, depending on the specific system being targeted. Some common approaches include:
1. Brute force attacks: In this method, the attacker systematically tries all possible combinations of keys or passwords until the correct one is found. This process can be time-consuming and resource-intensive, especially if the key space is large.
2. Cryptanalysis: This approach involves analyzing the cryptographic algorithms and protocols to discover vulnerabilities or weaknesses that can be exploited. It often requires expertise in mathematics, statistics, and computer science to identify patterns or flaws in the encryption methods.
3. Side-channel attacks: These attacks exploit information obtained from the physical implementation of the cryptographic system, rather than directly attacking the algorithms themselves. For example, an attacker may analyze power consumption, timing, or electromagnetic emissions to gain insight into the encryption process.
4. Key management attacks: Cryptographic systems rely on the secure storage and distribution of encryption keys. By targeting the key management infrastructure, attackers can gain unauthorized access to encrypted data or discover the encryption keys themselves.
5. Social engineering: Sometimes, the easiest way to break a cryptographic system is to trick the users into revealing their passwords or encryption keys. This can be achieved through various methods, such as phishing emails, impersonation, or psychological manipulation.
It is worth noting that breaking modern cryptographic systems, especially those widely used for securing sensitive information, is extremely difficult and often requires significant computational power and specialized knowledge. Many cryptographic algorithms are designed to withstand attacks and have undergone rigorous testing and analysis by experts in the field. However, as technology advances and new vulnerabilities are discovered, cryptographic systems must be continuously updated and improved to ensure their resilience against breaking attempts.
Importance and Future Scope of Cryptography
Cryptography plays a crucial role in ensuring the security and privacy of communication, data storage, and transactions in the digital world. It involves the use of mathematical algorithms and techniques to encrypt and decrypt information, making it unreadable to unauthorized individuals. The importance of cryptography can be summarized as follows:
1. Confidentiality: Cryptography helps maintain the confidentiality of sensitive information. By encrypting data, only authorized users with the appropriate decryption key can access and understand the content, preventing unauthorized access or eavesdropping.
2. Data Integrity: Cryptographic techniques can ensure the integrity of data, meaning that it cannot be modified or tampered with during transmission or storage. Any modifications made to the encrypted data will result in an invalid decryption, alerting the recipients to potential tampering.
3. Authentication: Cryptography also helps in verifying the authenticity of digital messages and entities. By using techniques like digital signatures, it allows users to verify the identity of the sender and ensure that the message has not been altered in transit.
4. Non-repudiation: Cryptography can provide non-repudiation, meaning that a sender cannot deny sending a message or carrying out a transaction. Digital signatures can serve as evidence of the sender’s intent and responsibility.
5. Trust in E-commerce: Cryptographic techniques are vital for establishing trust in electronic commerce. Secure protocols, such as SSL/TLS, encryption algorithms, and digital certificates, are used to protect online transactions, ensure secure payment processing, and safeguard sensitive customer information.
The future scope of cryptography is vast and will continue to evolve in response to emerging technologies and threats. Here are some key areas of focus:
1. Quantum Cryptography: As quantum computers become more powerful, traditional cryptographic algorithms may become vulnerable to attacks. Quantum cryptography aims to develop secure communication protocols that utilize quantum phenomena to guarantee strong encryption.
2. Homomorphic Encryption: Homomorphic encryption allows computations to be performed on encrypted data without decrypting it. This field holds great promise for secure data processing in cloud environments while preserving privacy.
3. Post-Quantum Cryptography: With the advent of powerful quantum computers, post-quantum cryptography research aims to develop new cryptographic algorithms and protocols that can resist attacks from quantum computers.
4. Blockchain and Cryptocurrency: Cryptography is a fundamental component of blockchain technology and cryptocurrencies like Bitcoin. The ongoing development and adoption of blockchain will drive the need for robust cryptographic techniques to ensure the security and privacy of distributed systems.
In summary, the importance of cryptography lies in its role in maintaining confidentiality, data integrity, authentication, and non-repudiation. The future scope of cryptography includes addressing quantum computing threats, homomorphic encryption, post-quantum cryptography, and supporting blockchain technology and cryptocurrencies.
Topics related to Cryptography
Abstract Algebra and Number Theory – YouTube
Abstract Algebra and Number Theory – YouTube
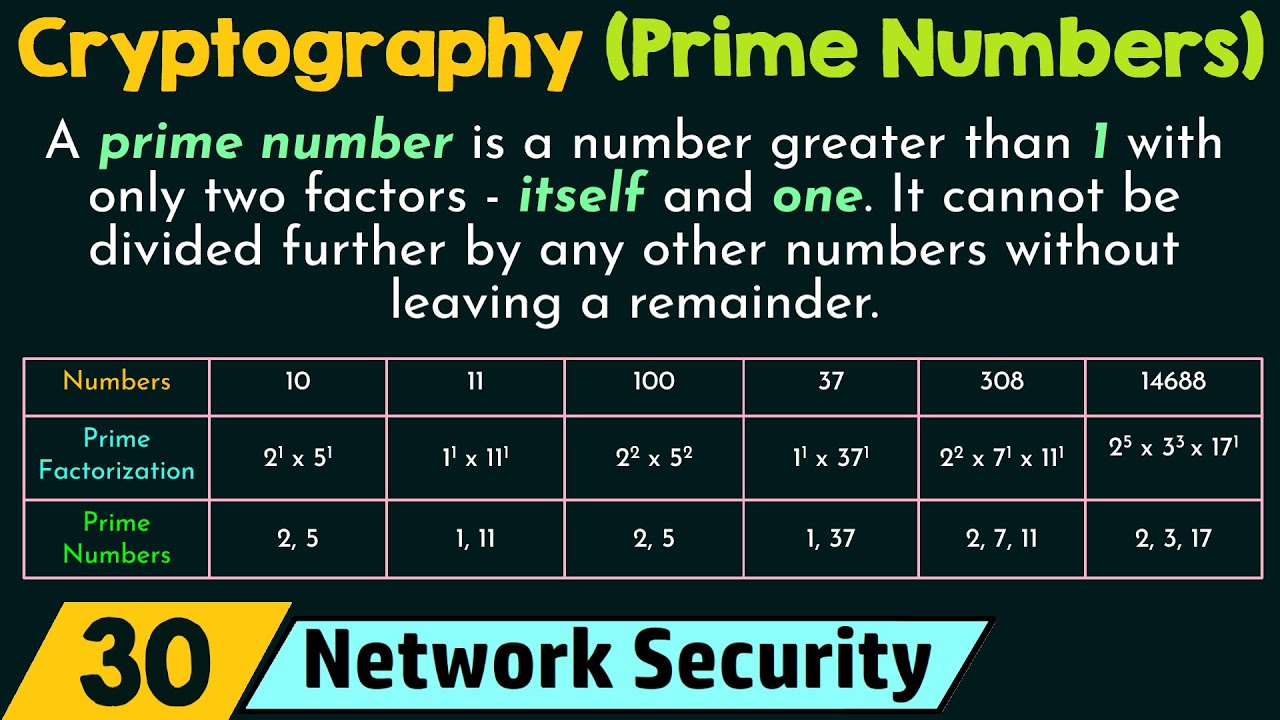
Prime Numbers in Cryptography – YouTube
Prime Numbers in Cryptography – YouTube
What is Cryptography – Introduction to Cryptography – Lesson 1 – YouTube
What is Cryptography – Introduction to Cryptography – Lesson 1 – YouTube
7 Cryptography Concepts EVERY Developer Should Know – YouTube
7 Cryptography Concepts EVERY Developer Should Know – YouTube
Cryptography | The Mathematics of RSA and the Diffie-Hellman Protocol – YouTube
Cryptography | The Mathematics of RSA and the Diffie-Hellman Protocol – YouTube
10 Math Concepts for Programmers – YouTube
10 Math Concepts for Programmers – YouTube
Lecture 1: Introduction to Cryptography by Christof Paar – YouTube
Lecture 1: Introduction to Cryptography by Christof Paar – YouTube
Lecture 2: Modular Arithmetic and Historical Ciphers by Christof Paar – YouTube
Lecture 2: Modular Arithmetic and Historical Ciphers by Christof Paar – YouTube
The Math Needed for Computer Science (Part 2) | Number Theory and Cryptography – YouTube
The Math Needed for Computer Science (Part 2) | Number Theory and Cryptography – YouTube
Lattice-based cryptography: The tricky math of dots – YouTube
Lattice-based cryptography: The tricky math of dots – YouTube

Peter Scholze is a distinguished German mathematician born on December 11, 1987. Widely recognized for his profound contributions to arithmetic algebraic geometry, Scholze gained international acclaim for his work on perfectoid spaces. This innovative work has significantly impacted the field of mathematics, particularly in the study of arithmetic geometry. He is a leading figure in the mathematical community.